One of the biggest advantages of Debian is the easy and mostly safe upgrade. It is extremely rare a Debian server to be “broken” after applying updates. To update a Debian server (as root or using sudo), simply give:
apt-get update && apt-get upgradeHowever, the server administrator needs to know when upgrades are available, which of them are security updates, how urgent is an upgrade, and if system reboot is required after system update. This how-to is mostly focused on these questions. This how-to is also applicable to Ubuntu (or other Debian based Linux distributions).
Get email notifications for updates
Many solutions are available. Our recommendation is apticron:
apt-get install apticron
Debian package installation will also create the Cron jobs. You may change scheduled time, if you want.
A sample apticron report:
apticron report [Sun, 10 Mar 2013 06:51:20 +0200]
========================================================================
apticron has detected that some packages need upgrading on:
cosmos.medisign.gr
[ 127.0.0.1 95.211.47.207 95.211.47.207 ]
The following packages are currently pending an upgrade:
perl 5.10.1-17squeeze6
perl-base 5.10.1-17squeeze6
perl-modules 5.10.1-17squeeze6
sudo 1.7.4p4-2.squeeze.4
========================================================================
Package Details:
Reading changelogs...
--- Changes for sudo ---
sudo (1.7.4p4-2.squeeze.4) stable-security; urgency=high
* Fix cve-2013-1775: authentication bypass when the clock is set to the UNIX
epoch [00:00:00 UTC on 1 January 1970] (closes: #701838).
* Fix cve-2013-1776: session id hijacking from another authorized tty
(closes: #701839).
-- Michael Gilbert <mgilbert@debian.org> Wed, 06 Mar 2013 18:41:15 +0000
--- Changes for perl (perl perl-base perl-modules) ---
perl (5.10.1-17squeeze6) stable-security; urgency=low
* [SECURITY] CVE-2013-1667: fix a rehashing DoS opportunity
against code that uses arbitrary user input as hash keys.
(Closes: #702296)
-- Niko Tyni <ntyni@debian.org> Tue, 05 Mar 2013 21:50:01 +0200
========================================================================
You can perform the upgrade by issuing the command:
aptitude full-upgrade
as root on cosmos.medisign.gr
--
apticron
From the apticron report, you already know which updates are security updates and you have an estimation of how urgent is to apply each update:
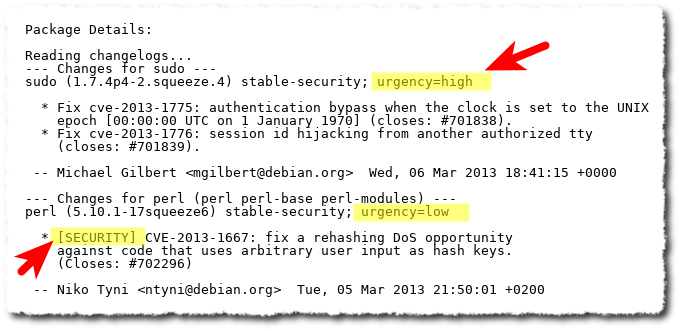
Which updates are security updates
Except of apticron report, you can find out which updates are available and which of them are security updates, using
/usr/lib/update-notifier/apt-check --human-readable
20 packages can be updated.
0 updates are security updates.
You need to setup update-notifier-common:
apt-get install update-notifier-common
Perform update
Use the following command (as root):
apt-get update && apt-get -V upgradeapt-get update updates the list of available packages (not the packages themselves).
apt-get upgrade actually installs newer versions of the packages (“-V” is useful to list the versions before and after update).
Example:
The following packages will be upgraded:
apt-show-versions (0.16 => 0.16+squeeze1)
base-files (6.0squeeze6 => 6.0squeeze7)
bind9-host (9.7.3.dfsg-1~squeeze8 => 9.7.3.dfsg-1~squeeze9)
dnsutils (9.7.3.dfsg-1~squeeze8 => 9.7.3.dfsg-1~squeeze9)
gzip (1.3.12-9 => 1.3.12-9+squeeze1)
host (9.7.3.dfsg-1~squeeze8 => 9.7.3.dfsg-1~squeeze9)
libbind9-60 (9.7.3.dfsg-1~squeeze8 => 9.7.3.dfsg-1~squeeze9)
libdns69 (9.7.3.dfsg-1~squeeze8 => 9.7.3.dfsg-1~squeeze9)
libisc62 (9.7.3.dfsg-1~squeeze8 => 9.7.3.dfsg-1~squeeze9)
libisccc60 (9.7.3.dfsg-1~squeeze8 => 9.7.3.dfsg-1~squeeze9)
libisccfg62 (9.7.3.dfsg-1~squeeze8 => 9.7.3.dfsg-1~squeeze9)
libldap-2.4-2 (2.4.23-7.2 => 2.4.23-7.3)
liblwres60 (9.7.3.dfsg-1~squeeze8 => 9.7.3.dfsg-1~squeeze9)
linux-base (2.6.32-46 => 2.6.32-48)
linux-image-2.6.32-5-amd64 (2.6.32-46 => 2.6.32-48)
openssh-client (5.5p1-6+squeeze2 => 5.5p1-6+squeeze3)
openssh-server (5.5p1-6+squeeze2 => 5.5p1-6+squeeze3)
perl (5.10.1-17squeeze4 => 5.10.1-17squeeze5)
perl-base (5.10.1-17squeeze4 => 5.10.1-17squeeze5)
perl-modules (5.10.1-17squeeze4 => 5.10.1-17squeeze5)
20 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
Need to get 0 B/40.9 MB of archives.
After this operation, 438 kB of additional disk space will be used.
Do you want to continue [Y/n]? y
Packages kept back
In rare cases you get the message:
The following packages have been kept back: packagename
in this case, use
apt-get update && apt-get -V --with-new-pkgs upgradeor
apt-get update && apt-get dist-upgradeFor details, see man apt-get (section
upgrade)
Check if reboot required
Reboot is required when kernel packages are updated. An easy way to detect this situation is:
/usr/lib/update-notifier/update-motd-reboot-required
*** System restart required ***
You need to setup update-notifier-common (see above).
IMPORTANT UPDATE (2015)
Debian Jessie does not include a update-notifier-common package. So check manually if system restart is required, checking if /var/run/reboot-required or /var/run/reboot-required.pkgs files existed
Example
cat /var/run/reboot-required
*** System restart required ***
cat /var/run/reboot-required.pkgs
linux-base
IMPORTANT UPDATE (2016)
Since Debian Jessie (and latest Ubuntu versions
of course), the package needrestart will do all the
job nice and easy:
Setup needrestart
apt-get install needrestartREAD DETAILS in this post: When to Restart Services or Reboot after Update on Debian or Ubuntu
Check which services need restart
Luckily, a system restart is required very rarely, after a Debian update. But, after installing new packages, some running applications may continue using older versions. This is also rare, but you can find out them with checkrestart
Example:
checkrestart
Found 5 processes using old versions of upgraded files
(5 distinct programs)
(5 distinct packages)
Of these, 3 seem to contain init scripts which can be used to restart them:
The following packages seem to have init scripts that could be used
to restart them:
openssh-server:
1853 /usr/sbin/sshd
ntp:
1161 /usr/sbin/ntpd
openvpn:
1445 /usr/sbin/openvpn
These are the init scripts:
/etc/init.d/ssh restart
/etc/init.d/ntp restart
/etc/init.d/openvpn restart
These processes do not seem to have an associated init script to restart them:
perl-base:
1092 /usr/bin/perl
python2.6-minimal:
1330 /usr/bin/python2.6
checkrestart is included in debian-goodies package. Setup it as usually:
apt-get install debian-goodies
IMPORTANT UPDATE (2016)
Since Debian Jessie (and latest Ubuntu versions
of course), the package needrestart will do all the
job nice and easy:
Setup needrestart
apt-get install needrestart
READ DETAILS in this post: When to Restart Services or Reboot after Update on Debian or Ubuntu
IMPORTANT UPDATE (2016)
Conclusion
- Get email notifications for updates: install apticron
apt-get install apticron - Which updates are security updates: check apticron report
- Perform update:
apt-get update && apt-get -V upgrade - Check which services need restart and if reboot is required:
install needrestart
apt-get install needrestart
Entrepreneur | Full-stack developer | Founder of MediSign Ltd. I have over 15 years of professional experience designing and developing web applications. I am also very experienced in managing (web) projects.
